Always Evolving.
Infinitely Intelligent.
Protect your organization from any threat with the world’s most advanced AI-powered cybersecurity platform. With SentinelOne, you can secure tomorrow.
The Value of
One Platform
Consolidate products, maximize value, and improve business continuity. See why 4 of the Fortune 10 choose the SentinelOne platform over other security vendors.
Reduce
Risk
0%
Faster MTTR with
no delayed detections
Reduce
Costs
0%
Reduction in
operational costs
Maximize
Value
0%
Savings in data
retention costs
Increase
Efficiency
0%
Improvement
in automation
AI Cybersecurity Built to
Protect Your Future
Equip your organization with the tools and intelligence to anticipate threats, manage vulnerabilities and protect your cloud, endpoint, and identity resources anywhere in the world. Combined with 24/7/365 threat hunting and managed services, SentinelOne is defining the future of cybersecurity with the Power of AI.
Protect the Endpoint
Securely manage your assets across your entire attack surface with AI-powered EPP, EDR, and XDR.
Secure the Cloud
The cloud is constantly evolving. Transform securely with real time cloud workload protection.
Fortify Identities
Reduce your Active Directory risk, detect and stop credential misuse, and prevent lateral movement.
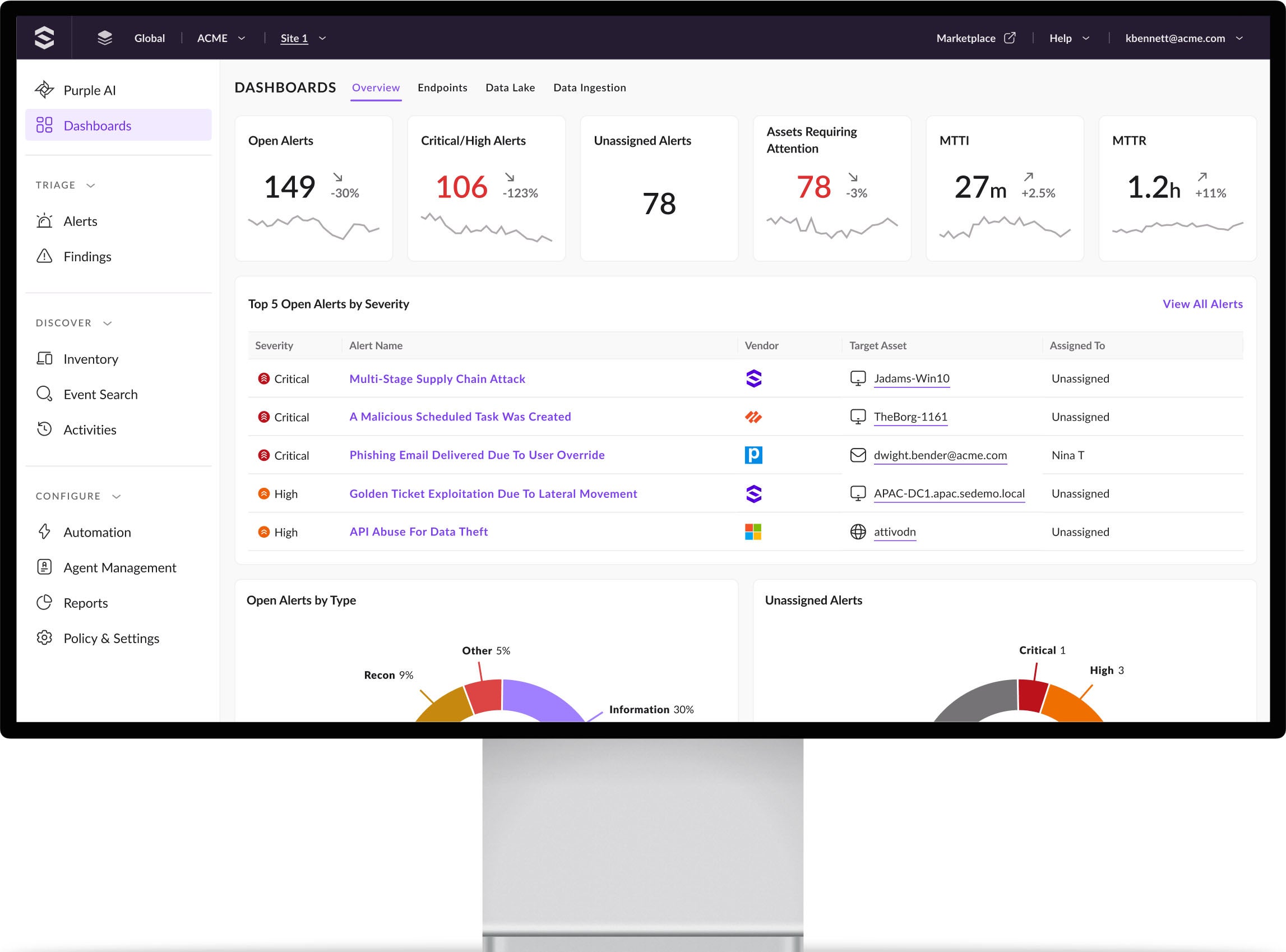
Turn Data into Actionable Insights
Centralize and Transform Data for High-Performance, AI-Powered Security and Log Analytics.
Accelerate SecOps with Industry-Leading AI
Detect sooner, respond faster, and stay ahead of attacks with Purple AI from SentinelOne—the world’s most advanced AI cybersecurity analyst.
Securing the Best of the Best
"I would describe SentinelOne in three words. Reliability, performance, and scalability.”
Raymond Schippers - Head of Threat Detection and Response at Canva
"Innovation is king and we have to move fast. SentinelOne gives us the confidence to move quickly, knowing that it has our back.”
Lou Senko - Chief Availability Officer at Q2
"We chose SentinelOne because of the protection. We believe out of the independent testing that SentinelOne is doing the best job in the market.”
Friedrich Wetschnig - CISO & VP Enterprise IT at Flex

"SentinelOne has changed the way we do cybersecurity.”
Tony Tuffe - IT Support Specialist at Norwegian Airlines
"SentinelOne was really like a self-driving car. It aided the team to do bigger and better things.”
Steve O’Conor - Director of IT at Aston Martin Lagonda LTD.
A Leader in Endpoint Protection. Again.
A Leader in the 2023 Magic Quadrant for Endpoint Protection Platforms
Record Breaking Attack Evaluation
SentinelOne leads in the latest MITRE ATT&CK Evaluation with 100% prevention
Leading analytic coverage, leading visibility, and zero detection delays.
96% Would Recommend For EDR & EPP
4.8/5 Rating for Endpoint Protection Platforms and Endpoint Detection & Response Platforms
1,000+ Five Star Reviews





